KeoNhaCai 88, Tỷ Lệ Kèo Nhà Cái 5, Kèo Bóng Đá Hôm Nay
Keonhacai đóng vai trò then chốt trong cá cược bóng đá, giúp người chơi nắm bắt tỷ lệ kèo nhà cái và xu hướng trận đấu chính xác hơn. Việc hiểu và phân tích kèo hiệu quả sẽ nâng cao khả năng dự đoán, tối ưu lợi nhuận khi đặt cược. Truy cập https://essaysonservice.com/ để khám phá thêm kinh nghiệm, chiến thuật soi kèo bóng đá chuẩn xác, cập nhật liên tục.
Hiểu hơn về Kèo Nhà Cái tỷ lệ cá cược – https://essaysonservice.com
Thật khó để có thể hiểu được công dụng của kèo nhà cái nếu như không biết được tại sao hình thức này lại xuất hiện. Trên thực tế, cá cược bóng đá hiện nay đang cực kỳ phát triển. Do đó, nhu cầu về những kèo bóng chất lượng người hội đam mê cá cược tham gia đang tăng cao. Chính vì thế, những công cụ phục vụ trực tiếp cho vấn đề này được hưởng lợi và càng ngày càng phát triển.
Keonhacai com được hiểu là một trang web, đúng hơn là một công cụ cung cấp tỷ lệ kèo nhà cái. Website này được tạo bởi một cá nhân hoặc một tập thể với mục đích duy nhất là hỗ trợ cho người đam mê kiếm lợi nhuận từ lĩnh vực này. Điều đáng quan ngại nhất trong một công cụ uy tín chính là sự chính xác. Vì nếu thiếu độ chính xác thì chỉ mang đến đau thương cho người sử dụng mà thôi. Và như vậy thì sẽ cực kỳ mất uy tín và sẽ không thể phát triển lâu dài.
Những tính năng được tích hợp tại https://essaysonservice.com
Hiện nay, có khá nhiều website dựa theo yếu tố này để phát triển. Trong số đó, sự uy tín luôn được thể hiện tại đây cùng với các tính năng cực kỳ chất lượng.
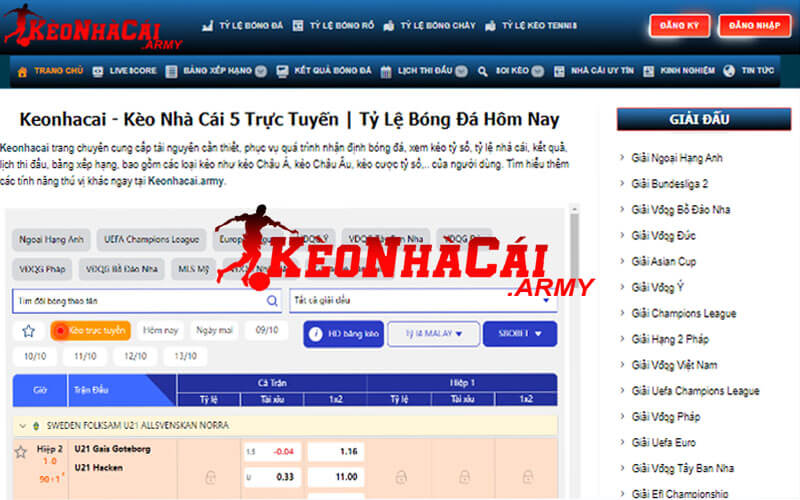
Soi kèo nhà cái 5 hằng ngày
Keonhacai thì chắc chắn không thể thiếu được tính năng quan trọng nhất. Đó chính là cung cấp kèo bóng đá được các chuyên gia tung ra thị trường. Kèo cược này chính là thứ mà người chơi hiện nay sử dụng để kiếm lãi thông qua lĩnh vực bóng đá.
Tại website https://essaysonservice.com/, chúng tôi cung cấp một chuyên mục chỉ để mang đến tỷ lệ kèo hôm nay chất lượng, uy tín và chính xác nhất đến cho người dùng. Tập hợp trọn vẹn các kèo bóng quan trọng như Handicap, kèo châu Âu và kèo Tài Xỉu. Người dùng hoàn toàn được quyền sử dụng kèo bóng này để sử dụng ở các nhà cái vì đây là kèo chung được phổ cập mỗi ngày.
Nhận định kèo bóng đá hôm nay
Keonhacai không chỉ cung cấp kèo bóng dành cho người tiêu dùng. Tại đây, chúng tôi còn sở hữu đội ngũ chuyên gia. Họ chuyên phân tích những dữ kiện xung quanh các cặp đấu để thực hiện nhận định và dự đoán kết quả của từng kèo bóng.
Tính năng này được chúng tôi tích hợp vào chuyên mục Nhận Định. Người tiêu dùng hoàn toàn có thể truy cập vào để sử dụng nhằm mục đích phục vụ cho quá trình cá cược của bản thân.
Tin tức bóng đá mỗi ngày
Keonhacai sở hữu đội ngũ phân tích bóng đá, vậy lượng tin tức để những chuyên gia này sở hữu lấy từ đâu. Chắc chắn rồi, đó là từ những phóng viên của chúng tôi. Những nhân sự này được phân bố ra khắp các giải đấu trên toàn cầu để thu thập thông tin.
Tin tức bóng đá sẽ được cung cấp thông qua dạng bài viết được đặt tại chuyên mục Tin Tức Bóng Đá. Người dùng hoàn toàn có thể nắm được các thông tin quan trọng trong lĩnh vực bóng đá. Đặc biệt là xung quanh cặp đấu chuẩn bị diễn ra trong ngày để nhận định được tốt nhất.
Lịch thi đấu và kết quả trong từng giải đấu
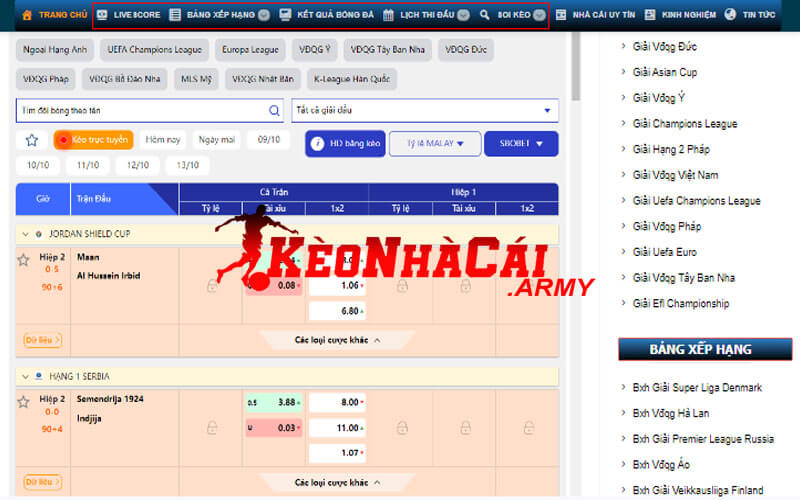
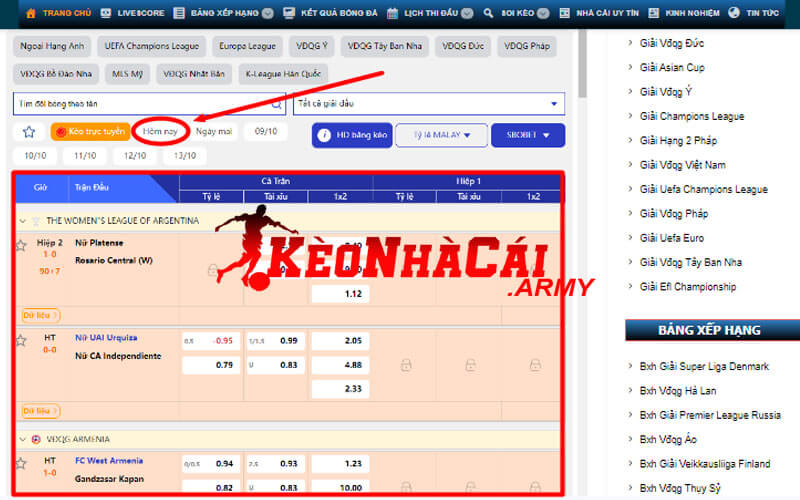
Keonhacai kết hợp việc thu thập tin tức với việc thu thập những dữ kiện liên quan trọng từng giải đấu. Hiện nay, chúng tôi cung cấp kèo bóng đá của những giải đấu hàng đầu. Song song với đó là lịch thi đấu, bảng xếp hạng và kết quả bóng đá trong từng cặp trận.
Thông tin này đóng vai trò rất lớn trong những dữ liệu mà chúng tôi cung cấp. Vì vậy, sự chính xác và uy tín luôn được đảm bảo để không khiến người dùng nghi ngờ. Chúng tôi sẽ trở thành một công cụ cực kỳ tốt để phục vụ người đam mê cá cược bóng đá toàn cầu.
Trực tiếp kèo nhà cái
Keonhacai đồng hành cùng người chơi tại chuyên mục Livescore. Đây là chuyên mục chứa tính năng theo dõi diễn biến của những trận đấu đang diễn ra. Tại đây, người chơi sẽ có thể theo dõi được nhiều trận đấu cùng một lúc để hiểu những gì đang diễn ra trên sân bóng.
Tính năng này rất quan trọng trong quá trình đánh rung và đánh góc nhiều trận cùng một lúc. Hoàn toàn cần thiết cho những chuyên gia để kiếm lợi nhuận thông qua lĩnh vực này.
Các kèo bóng phổ biến tại Keonhacai
Kèo nhà cái trực tuyến tập trung chủ yếu vào việc cung cấp kèo bóng và tin tức bóng đá cho người dùng. Sau đây là các kèo bóng phổ biến được hiển thị tại đây.
Kèo Handicap
Handicap hay còn được biết đến với cái tên thuần Việt hơn là kèo chấp hoặc kèo châu Á. Đây là kèo sử dụng tỷ lệ ăn thưởng Malaysia. Về hình thức, Handicap có nghĩa là đội được đánh giá mạnh hơn sẽ chấp đội yếu hơn một cơ số bàn thắng nhất định trong trận.
Người chơi cần phải dự đoán tỷ số và trừ đi những trái chấp để đưa ra kết quả chính xác. Chỉ khi kèo trên thắng với cách biệt vượt qua cả số bàn chấp thì mới giành được chiến thắng.
Kèo Tài Xỉu
Keonhacai chắc chắn không thể bỏ qua được kèo bóng người tiêu dùng hiện tại yêu thích nhất. Cái tên Tài Xỉu thì đã quá quen thuộc trong lĩnh vực cá cược hiện nay. Đây là thuật ngữ xuất hiện ở nhiều trò chơi đỏ đen với ý ám chỉ là người dùng phải đặt kết quả trên hoặc dưới con số mà nhà cái đưa ra.
Đối với bóng đá, hình thức của loại kèo này cũng tương tự. Kèo nhà cái 5 sẽ cung cấp một con số nhất định dành cho cặp đấu. Người chơi cần phải đặt cược vào vị Tài (lớn hơn) hoặc Xỉu (nhỏ hơn). Kết quả được tính dựa theo tổng số bàn thắng đã ghi được trong 90p của trận đấu.
Kèo châu Âu
Keonhacai mang đến cho người tiêu dùng kèo bóng quan trọng cuối cùng trên bảng cược phổ biến. Cái tên kèo châu Âu hay kèo 1×2 đã qua quen với những người đam mê bộ môn này.
Người chơi cần phải tuân thủ keo nha cai khi việc cần làm để tham gia chính là lựa chọn đội giành chiến thắng. Trông thì rất dễ nhưng khi tham gia mới biết nó phụ thuộc rất nhiều vào kỹ năng lấy thông tin. Điều quan trọng, có vị cược Hòa để người chơi đặt cược nếu muốn và kèo 1×2 không áp dụng kèo chấp vào đâu nhé.
Kết luận
Keonhacai cung cấp những kiến thức cần thiết cho quá trình nhận định bóng đá của người đam mê. Công cụ này hiện đang được cụ thể hóa một cách uy tín tại https://essaysonservice.com – truy cập và sử dụng ngay hôm nay.










